Darren’s Diary
Student Name: Huan Meng
Blog: http://mhuan.name/
E-mail: darren@mhuan.name
I hereby declare that the contents of my diary are my own words, unless otherwise clearly marked.
23 Sep 2010
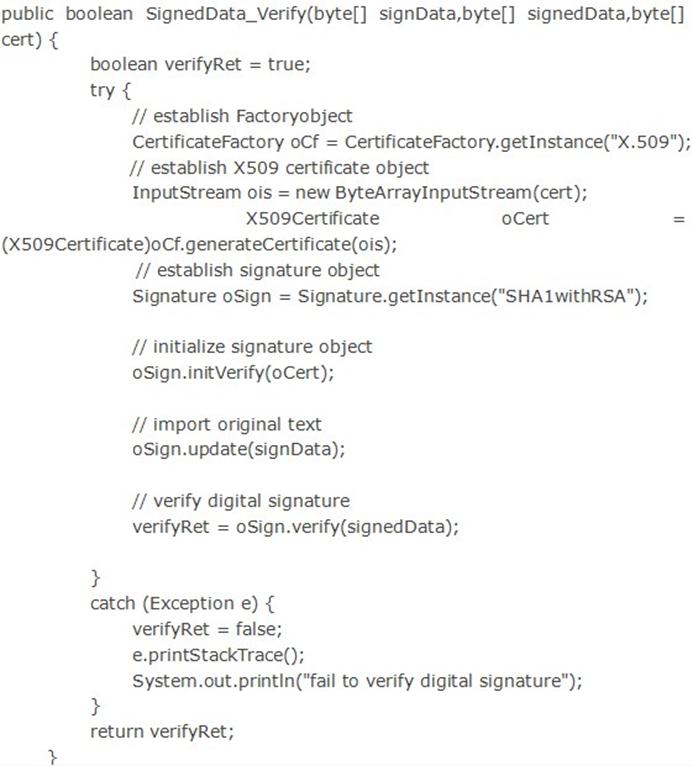
We talked about Access Control Policies, I’ll give my ideas and some questions about these polices.In Discretionary Access Control (DAC), although a system administrator controls the access, a user has the right to allow or refuse an access which he sets to an object. This control is based on the identities of both subject and object. That is why it is also called an identity-based access control (IBAC). A DAC based system has an Access Control List (ACL) on each resource object, which reflects the user has the allowed access to who he maps with. DAC is used in most desktop operating systems because of its flexibility, but there it also expands the risk and threats.
Unlike DAC, Mandatory Access Control (MAC) is strict that the access is controlled by the system and can not be changed or altered by users. All the information between subjects and objects will be checked by the system which gives the permission for them. Compared with DAC, MAC is based on security label which contains a classification and a category to resource objects. When a user wants to access an object, these two pieces are always checked whether they are the same with the user’s certificate. So in the Bishop’s book, it is said that it is occasionally called a rule-based access control, but in which occasion can it be called this? In Rule Based Access Control (RBAC), access is also allowed or denied by the system, neither the subject nor the owner of the object. I think it’s the similarity of both policies; the difference is about the rules and the rules always exist in these policies. So can we say the security label has some rules for MAC? Furthermore what about the rules in ACL? If we can, what’s the difference between MAC and RBAC?
In Originator Controlled Access Control (ORCON), the creator of an object has the right to control the object and the access to the object. So a subject can give another subject rights to an object only with the approval of the creator of that object. ORCON makes the originators of documents retain control over them even after those documents are disseminated. This is more advantageous than MAC/DAC in handling such environments.
Role Based Access Control (RBAC), also known as Non discretionary Access Control, takes more of a real world approach to structuring access control. Access under RBAC is based on a user’s job function within the organization to which the computer system belongs. So it is an actual policy for each role in different circumstance.Although there may be few rights for the user acted as a role in a system, it is a good way to control the permissions appropriately and it is also effective to protect the whole system.
21 Sep 2010
After the lecture, I studied the Bishop’s book about access control mechanisms-ACLS and Capabilities combined with the review of Access Control Matrix in Chapter 2.
In my opinion, although ACM is the abstraction mechanism, its clearest and purest form can make us understand any expressible security policy. Considering that many systems have too many objects and subjects who need much space, the ACM give simple way to analyze the security problems.
Access control mechanisms explain how to control the subjects and objects. In ACL which binds the data controlling access to the object,
I learned that:
It can limit network traffic and improve network performance. For example, ACL can specify the priority of the data packets according to the protocol of packets.
It provides means of communication traffic control. For example, ACL can restrict or simplify the length of the routing update information, thereby limit the communication flows in some network segments of a router.
ACL provides the basic means to secure the access to the network. E.g. ACL allows host A to access to the network of human resources, and refuses host B to access.
At the port of the router, ACL can decide which type of traffic is forwarded or blocked.
18 Sep 2010
In lecture seven, we talk about some methods of password cracking and how to choose a good password as well as how to make it valid secretly. So I will explain about these topics with my conclusion and opinion.
Password cracking:
1、Exhaustive attack: A trial-and-error attempt to violate computer security by systematically attempting to use a very large number of possible passwords or keys.
2、Dictionary attack: A dictionary file (a text file full of dictionary words) is loaded into the crack applications (such as LophtCrack), which runs based on the user account targeted by the application. Because most passwords are usually simple, running a dictionary attack is often sufficient to achieve the purpose.
3、Hybrid attack: Hybrid attack will add numbers and symbols to the file name to crack the code successfully. Many people change the password just by adding a number after the current password. The model commonly used in this form: The password is “cat” first month; the password of next month is “cat1”; the next password is “cat2”, and so on.
4、Social engineering scam: It utilize small public trick to lead the victim into a trap. This technique usually achieves by talking, cheating, using forgery or spoken words to legitimate users in order to get user list, user passwords and network structure.
5、Sniffer: Network “sniffer” allows an attacker to view the network traffic in real time. From these movements, they can pick out interesting data, including password which is lack of protection. Using IPSec and Kerberos security protocols can protect valuable data from being decrypted so that the sniffer can only record useless information.
6、 Trojan horse: A Trojan horse software that looks harmless will induce users to allow them to run. Once these programs run, they can use the user’s context through a variety of ways to attack the network. It can be done including monitoring the user’s keyboard input and sending them to third parties. For example, when users access to non-domain resources required to enter a password to be authenticated, the Trojan can intercept the user’s password.
15 Sep 2010
In today’s lecture, Alan gives us a question about the difference between authentication and identification. From the Bishop’s book, authentication is defined as the binding of an identity to a subject. As far as I’m concerned, it is like someone should prove who he is. So he must provide information to confirm his identity, maybe his face, voice, DNA, a key or a password. The information can be looked as his specific identities relatively, but they can also be counterfeited. Therefore, the process of recognizing the information is called identification and we must be sure that these identities are accurate and believable. Only when these identities are checked and verified in a process of an identification, we can say the authentication is OK. So this is my understanding of their difference, but it’s also hard to tell the difference between authentication and identification, so what’s the real difference of them? How to compare or contrast?
Comment by IoannisKakavas :
You can map the difference between identification and authentication as following Identification is the process when you say that you are Darren ( For instance providing a username ) Authentication is the process when you actually prove that you are Darren ( Providing the correct password that is associated with this username)
12 Sep 2010
In One-Time Pad, the key string is chosen at random and we use the random key only once. It is difficult to break using large scale computer theoretically, but in practical, it is impossible to break. One-Time Pad idea has already been used as the safest key in some banks and game account. For example in BOC, we use E-token as our key for e-bank, the 6 digits key changes every minute irregularly, and the key can be used only once before it changes. However, it’s also a relatively safe way on the internet. Attackers can use “Phishing” website, Trojan horses to get users’ account information. These users also suffer from Stealing DC, bugs of ID authentication and so on.
In the public key system e.g. RSA, we can use a pair of public key and private key to provide a type of nonrepudiation of origin, which is a kind of authentication to ensure that the message is from certain people e.g. digital signature. In the encryption of RSA, even though we can make the n large enough, there are some risks that the message can be changed or broken. The attacker often adopts “forward search” or “precomputation” to change the order of the blocks, which may lead to wrong information or get some simple message comparing the ciphertext he enciphers from a public key with that he intercepts from the originator.
8 Sep 2010
We’ve talked about basic cryptography in this lecture. Alan presents Caesar cipher as an example to illustrate some aspects and elements in cryptography.
Enciphering functions: E = { Ek | k ∈ K and for all m ∈ M, Ek(m) = (m + k) mod 26 }
Deciphering functions: D = { Dk | k ∈ K and for all c ∈ C, Dk(c) = (26 + c k) mod 26 }
Caesar cipher is so weak, because it is easy for others to find the key with only the ciphertext in a ciphertext only attack, with the ciphertext and the plaintext enciphered In a known plaintext attack or with specific plaintexts enciphered In a chosen plaintext attack. The keyspace is small,
Cryptography has two common cryptographic algorithm for the symmetric cipher algorithm (single-key encryption algorithm) and non-symmetric encryption algorithm (public key encryption algorithm). DES and RSA represents each of the algorithms. But it is hard to say which is better. They have their own advantages in some aspects of algorithm, such as processing speed of algorithm, key allocation and so on.They are used in different kinds of field and the security of both of them is relatively high. There are lots of other algorithms in this area and which we should choose is based on our demands.
4 Sep 2010
From yesterday to today, I read the book Introduction to Computer Security and put these three lectures and slides in order systematically in my mind.
I read about CIA(Confidentiality,Integrity,Availability) again combined with the access control matrix model. Access control mechanisms support confidentiality by cryptography and other system-dependent mechanisms which can preserve confidentiality better than the former, when the controls work well based on an ideal good access control matrix model. I think this is the most important way to support confidentiality compared with cryptography or resource hiding. But the point is that the access control matrix model is an abstract model and there is no such a perfect particular implementation or system which never fails. From the the generality of the AC matrix, I’ve seen AC matrix example on a LAN and a program and how rights work as entries in this two AC matrix. The relationship between subjects and objects is hard to balance in AC matrix. The rights for both of them, such as “write”,”read”,”append” and “execute” between processes and files, depend on the instantiation of the model and you can never make sure these functions are always easy undertook.
There is also a question about Alan ‘s bank account balance: Balance(t)=B(y)+D(y)-W(y), how does it work and why?
Comment by Spyridon Dossis : Concerning your question about the bank account balance, i think you mention a characteristic example that is given to point out the importance of data integrity especially in commercial environments. The equation represents a normal operation that can happen in a bank system where the calculated Balance in the end of each day must be equal to the sum of previously deposited money plus the current’s day deposited one minus the withdrawn amount. Therefore e.g. when a program changes a value, the system must impose a rule that such a equation must always be valid, in order to ensure the consistency of the data. You can read more about this topic in the course book in the section of Clark-Wilson Integrity Model. A relevant topic from enterprise and database systems is the notion of transactions. There a complex operation consisting of a set of simpler one operations (like additions or subtractions as in the previous example) must either be performed successfully as a whole either in the case of even one failed intermediate step the whole process must be roll-backed and the initial state of the system recovered. See Transaction processing for more on this. The main aim of this is to preserve the integrity and consistency of system’s data.
2 Sep 2010
I have found many information about this course on FirstClass and also understand how to get information, discuss with others, how to learn this course through this powerful tool. I’ve already cleared up my mind and made a study plan. I think this preparation is a good start for my study.
I once compared some treats listed in the first lecture and found that DoS/DDoS do a great threat to those companies in China. A company based on IM which is called TX suffers from those attacks and threats. Because of the unripe network in china, the company invest much money and manpower on security for their data of custom and other secrets. There is no definition of security, the ideal model of security is to find threats prior, but it is impossible yet. Any defense is base on pre-existing knowledge or some caculation, there are little ways to discover potential threats actively. The criminals for security are always happening and the defense and fights against those attacks will never stop.
Reference
Bishop, Matt. Introduction to Computer Security, Addison Wesley, 2005.

![]()