在KTH做的第一个比较有意思的实验,虽然个人觉得有点无聊,不过老师们貌似都挺感兴趣,和大家分享下,欢迎点评。
| Keywords: | Face Recognition,Masquerading, Filch, Counterfeit |
| Date: | 2010-10-11 |
| Status: | Complete |
| Prerequisites: | Computers with windows system, Ability of Image editing, Face recognition system, Camera, Printer |
| Person hours: | To complete: 48 person-hours To repeat: 30 person-hours |
| Educational value: | *****_____ |
| Booked by: | Huan Meng ( huanm@kth.se ) & Jing Ba ( jingb@kth.se ) |
Copyright: Huan Meng ( huanm@kth.se ) & Jing Ba ( jingb@kth.se )
Autumn Term 2010 Proposal
FaceRecognitionAttack
Summary
Now the face identification has been used in many security areas. We can get the pictures of victims from video chat, a photo and so on, then use these information to have a unauthorized access to a system with face identification mechanism.
Goals
Try to Invade a system with ASUS Smartlogon face identification by using a counterfeit of face recognition and analyze some feasible solutions.
Method
1.analyze the principle of operation about the face identification and ASUS Smartlogon system
2.filch the pictures of a familiar person’s(the victim) face(from video chat, photos or some samples from his computer).
3. process the images and make some facial image samples of victim.
4.access the victim’s system with a counterfeit face identification.
5.analyze the attack and some solutions to deal with the attack.
Introduction and Smartlogon analysis
Facial recognition is a digital application used to identify and verify the identity through digital images or videos.
In our this assignment,the target is the software called Smartlogon.In this software,it has used the feature-based recognition algorithms and appearance-based recognition algorithms.So the method of facial recognition it uses is mainly the method with geometrical character.Because of this method,the identification application has its deficiency,we can just use the image replacement to cheat it when we need to log on.According to this point,we can attack the identification application through stealing photos in victim’s PC and printing screen[1].
After checking the documents about the software,we can find a database in this software to reserve the users’ images.The database saved hundreds of the user’s images.And we find that it takes dozens of photos from user everytime,then the algorithm synthesizes these photos and makes a integrative image to be the identification standard.So we can intromit some our own images in order to diluting the standard.But there is one thing very important,it’s that we have to intromit enough images.
Traditional techniques
The basic method:
1.Face recognition using geometrical character
This method uses the geometrical relationship between the facial organs such as the interval.
2.Method based on eigenface(PCA) [2]
This method is based on KL transformation which is the optimal orthogonal transformation about image compression.
3.Neural network method
This method uses the study capacity and classification ability of neural network.
4.Elastic graph matching method [2]
This method uses zeniths in topological diagram to express facial eigenvector,then records the information around the zeniths.
5.LHD method
This method uses distance of the line sets extracted from the facial grayscale images.It’s a better choise in some different light conditions.
The algorithms used in the facial recognition:
1.Feature-based recognition algorithms
2.Appearance-based recognition algorithms
3.Template-based recognition algorithms
4.Recognition algorithms using neural network
5.Illumination pretreatment based on Gammar gray-level registration[3]
3D-method:
This method uses not only the distance of the specific facial organs,but also the individual features of one organ such as the height and depth.So it could avoid the affection from the lighting.And it could finish the identification within different angles. [9]
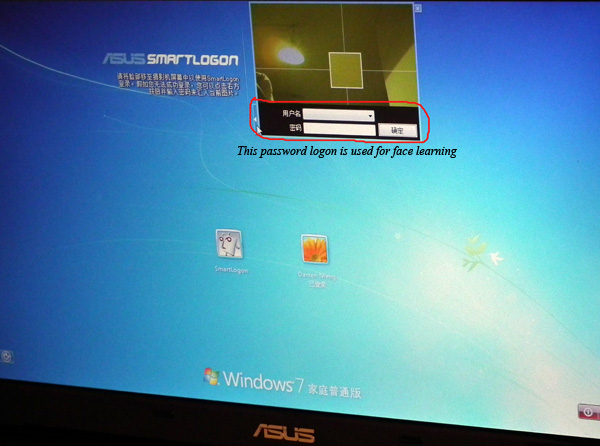
ASUS Smartlogon Setup:
Click the link below to download ASUS Smartlogon:
http://asus-smartlogon.software.informer.com/
ASUS Smartlogon analysis:
Principles of Face recognition
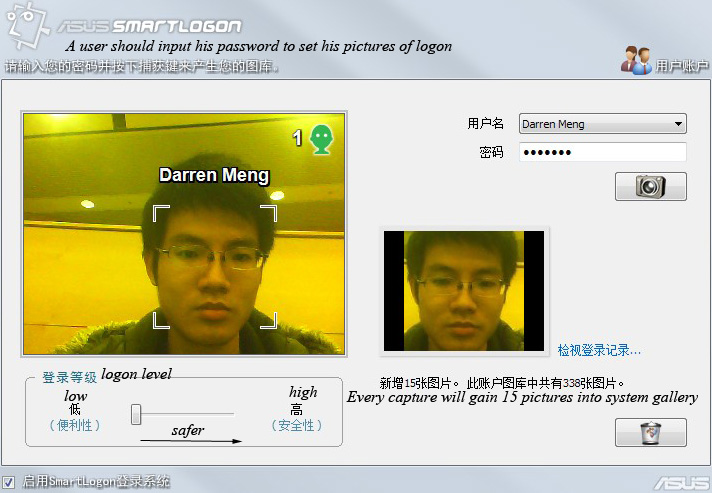
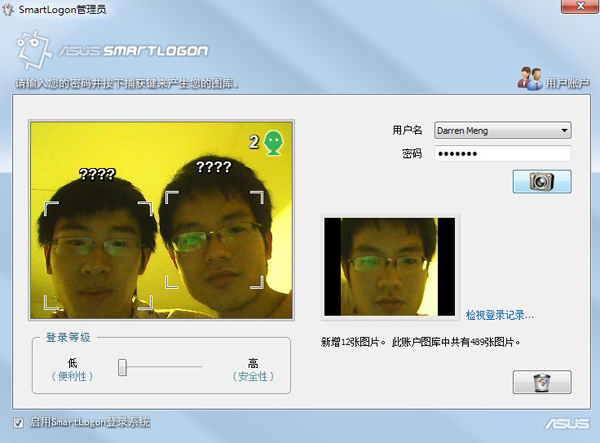
1. Select a user name and enter a password. Your password is used when for some reason your face fail to logon to Windows.
2. You can change the security level using the slider in order to better protect your Notebook PC You can change the security level using the slider in order to better protect your Notebook PC from others logging on but may also block yourself if you change your appearance. (Your typed password can still be used to logon.)
3. Before a face is registered, question marks will appear above the head. The number 1 or 2 in the top right of the camera screen is the number of faces detected. This face recognition can capture several people’s faces simultaneously and identify the user.
4. After you registered a face, the user’s name (here is Darren Meng) will appear above the head.
Principles of Logon Process
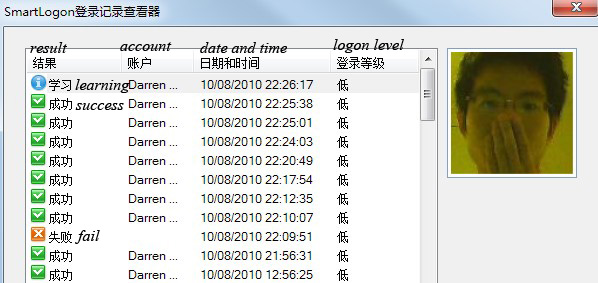
1. Users can view this log to check when someone tried to login with face detection on your computer.
2. There are three results “Success”, “Fail”, and “Learning”. Learning is gained when a user inputs a password to login and face captures are imported (red circle above).
Options
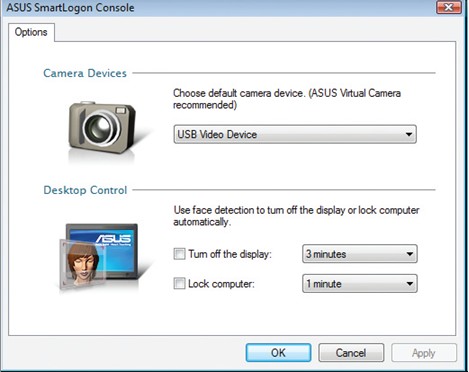
Camera Devices: The built-in camera is selected as default. Change if necessary.
Desktop Control: Check box and set timer to enable. See previous “Menu Items” for descriptions.
ASUS Smartlogon database
C:\Program Files (x86)\ASUS\SmartLogon\log\image
This file records the every image which is successful to logon Windows.
C:\Program Files (x86)\ASUS\SmartCore\gallery\d98cd74f-2f8a-44c1-b8ee-e5dde17ea6d2\imageThis file is used to store the captured images.
It is the Smartlogon database of all the user’s face images which are combined and analyzed with an algorism in order to provide the logon standard for a legitimate user.
Attack Details
Used Tools:
1. Photopaper and Camera FinePix HS11
We choose to use digital camera because of its excellent imaging and high resolution, which makes it possible to obtain photos with good quality and also makes it easier to extract clear face pictures from a photo. [5]

2. Laser Printer
Altough a laser printer has the advantages in speed and economy, we choose to use it mainly because of its precision. A printed picture is very different from developing the photos and the former one has low glossiness and definition. But if we use a high resolution picture with photopaper, the result of using a laser printer will change a lot. Make sure that your samples are enough to obtain a clear picture. [6]

Step1: Try to obtain a familiar victim’s face photos
Because the face recognition of Smart logon is based on the database of gallery and the rate of success logon depends on the light and PCA (Principle Components Analysis), we should use different ways to get victim’s different face samples to increase the rate matching the database and pass the logon detection. Here we adopt three methods to get picture samples in order to get proper counterfeit pictures, these methods are as below:
1. Obtain pictures from video chat with victim
We use an IM with video chat function to try to convince the victim using video chat. Then we capture several face pictures of victim during video chat. The image definition is based on the victim’s camera. The advantage of this method is that we can get the victim’s face picture directly, because we often use our head portrait during the process of video chat. Although the image definition may be low most of the time, we can edit and make them look better.
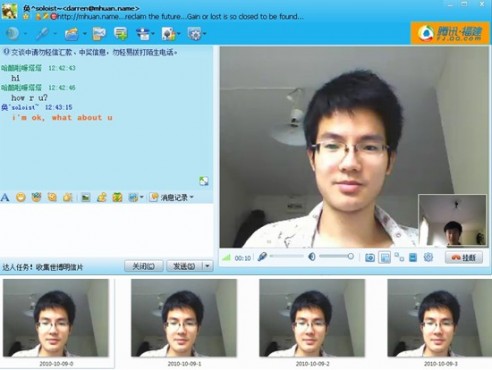
2. Obtain pictures from some victim’s life photos.
It is relatively easy to get a familiar victim’s life photos. When we go to travel or take some photos in daily life, we can get those pictures from camera. A digital camera and DSLR (Digital Single Lens Reflex) can make high quality photos, but they are usually not single face pictures, so we must extract the face pictures from those photos and the editing is also important.

3. Obtain some samples from the familiar victim’s computer
When we have the opportunity to use a familiar victim’s computer, we may find some samples of his or her face pictures (especially the picture database of SmartLogon). But the fact is that these pictures are always in small sizes and not clear enough to make a counterfeit photo. However we can refer to contrast level, brightness level and tones of pictures when we edit those face pictures.
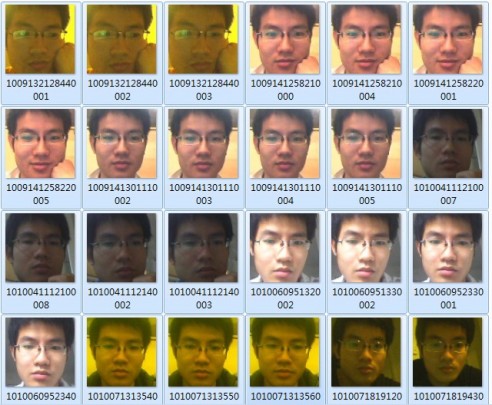
Step2: Choose some good pictures and edit those victim’s face pictures
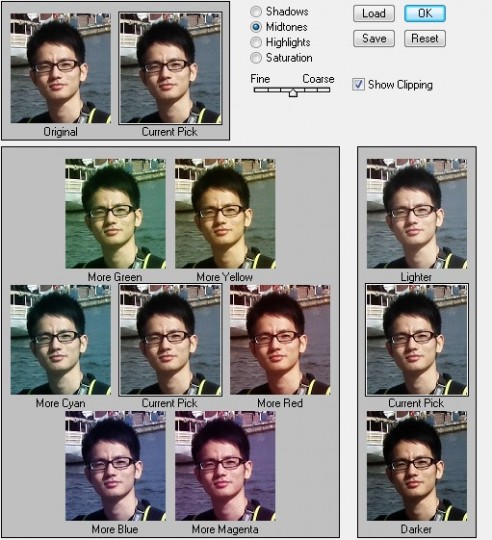
We will choose some face pictures from the three methods, combine them and edit them. By using Photoshop CS4, we can adjust the size, contrast level, brightness level, tones of pictures and so on, these are the most important elements for a picture, hence they also determine the rate of success logon. These are the most important elements for a picture, hence they also determine the rate of success logon.
So we give an editing scheme to those obtained pictures in order to cover more aspects of face pictures. By using this way, we can use the least samples to reach our goal. In consideration of the definition of the third method, we can not use these pictures to make a sample, but we can know some information about the database of the gallery which will help us make better samples. These are the editing methods we choose:
Editing for life photos
We cut the extra part of the photo first, what we need is just the head portrait. Notice that you should leave more space around the face rather than cut them all.
Because the picture from a digital camera has a good exposure and color, we mainly focus on changing the tone of the face picture.
As we know, the environment and the tone are very important for this kind of face recognition technique, so we should try to match the general situation considering of the different tones.
Editing for video chat photos
These photos are obtained from screenshots during video chat, so the quality is relatively low compared with a digital photo, but they have a more effective performance in the outline of face because of the direct captures on face. In this way, we may gain a higher rate of success logon when the face recognition system identifies the picture.
For these pictures, we should change the contrast, brightness and color saturation to make the captured pictures clearer and easier to be identified.
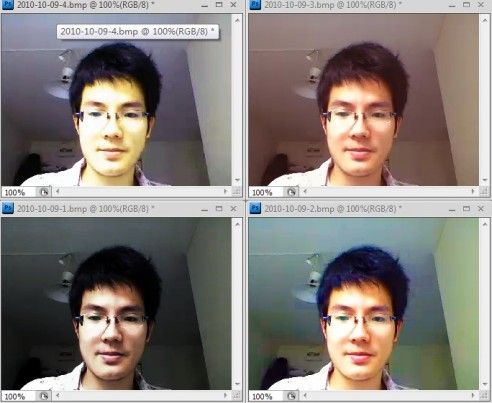
Step3: make some samples with these edited face pictures
After editing the obtained pictures, we need to print them by using a laser printer.
Note that the quality of a photo paper is very important to get verisimilar samples of face pictures, if you use a common paper to print those samples, the rate of success logon will be reduced much. One side of a photo paper is smooth and using a good photo paper will increase the brightness and color saturation of a picture, and it can gain the sense of layers, which makes those pictures more vivid. [4]
In the meantime, choose an advanced laser printer is also crucial.

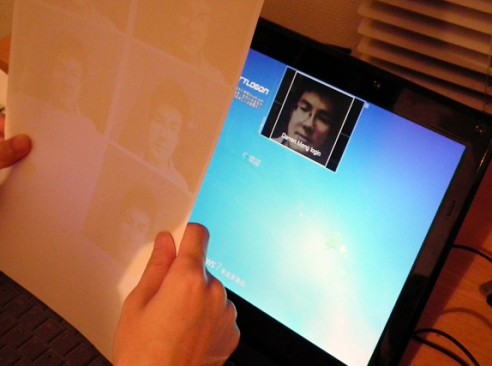
Step4: invade the victim’s computer with a counterfeit face identification
Try to access the victim’s computer with those printed samples. This process is to cheat the Smartlogon and let it recognize our counterfeit face portrait. Use your samples carefully, when you pick up your samples, leave some space around the face pictures. If the computer can not identify the pictures quickly, don’t worry and just try to change the angles with patience. You should try to use every sample one by one to check which one can match most.
We have already uploaded the whole process to Youtube:
http://www.youtube.com/watch?v=Y6eKNV9foTo [8]
Conclusion
In this experiment, we attack the facial recognition software with counterfeit face pictures successfully. Finally, the optimum picture is the one edited from video chat. It shows that the video chat picture is more proper because the user adopts this way to set the logon. The key of the process is the image samples. If the attackers can easily get the images of a victim, they can use the photos to make counterfeit pictures to access the system unauthorized. And also, with a good design or editing ability, an attacker may create your samples more like yourself. ASUS Smartlogon uses the compound information of these photos set by a user in database and it also has an algorithm to identify the face when we try to access the system. Because of the limitation in the algorithm in plane identification and the technique Smartlogon adopts, it’s possible to invade the system by this way.Through this experiment, we can find that there are following keys in this kind of facial recognition.
1. Similarity: The faces and the facial organs of different people have similar structure, so software sometimes is hard to distinguishing the faces in details, which makes it possible to forge a face pictures.
2. Mutability: The lighting, expression and angles could affect the images of faces, so it can’t ensure that every time we log on the system, there are the totally same images appearing in front of the camera. The environment around a face can make a big difference.
Now with the fast development of the science, there have been some effectual methods approved. For example, the 3D method uses the depth and height of the facial organs to increase the characters for identification. So it can increase the security level of the facial recognition. Some more advanced methods include the elastic graph matching method which provides the treatment about the elastic deformation caused by expression change and the multiple light source method based on infrared ray which could deal with the affection from lighting and angles. [8]
Difficulties we face:
1. The lighting and angles
In the experiment, we can’t access the system protected by facial recognition just by the original photos because of the differences on lighting and angles between these photos and the source reserved in database. So we have to edit the photos to match the images, but how we edit is very crucial to determine the result.
2. Matching probability
In these attacks, although we invade the system successfully, we just used several photos. Because of the affection from the lightness, angles and expressions, the success rate is a little low. In fact, we are against our low matching probability by making more efforts on pictures editing in order to get a good result. However, if possible, we should consider of comprehensive factors.
Shortages in our attack
1. High level mechanism
In this experiment, we just attacked some lower security level recognition. If the system is protected by higher levels, the face identification will be strict. Generally, a user will not choose to use a high level security, because with that level, the user himself may hard to logon with the different logon environment. But if it does, we may need to use some techniques such as the three-dimensions and thermal imagery.
2. Sample space
Theoretically, we’d better use victim’s photos as many as possible in this method. Compared with a handful of photos we use a large number of samples will get a good result. Few pictures can’ not match the characters of the face enough because the application uses the compound results to identify. We think a large number samples should be made if possible.
Other possible improvement
Our attack is based on the face recognition detection when an attacker login. So our method is to make a counterfeit photo. But indeed, the logon identification is just one aspect of face recognition. There is an assumption and possible improvement we give to make further attack, which we think is supposed to be more exact. We can attack the database and find the short of algorithm in identification process. E.g. we can add an unauthorized people’s pictures into the Smartlogon’s gallery database so that the unauthorized people may access the system with Smartlgon by using his own face. If we do so, we should intromit the photos to the database of the identification application and this method needs enough images of attackers[9]. In the meantime, if we can find the algorithm of Smartlogon, we can also analyze the algorithm about how the Smartlogon identify these photos. However, this method has a shortage that victims can check the picture’s information in the database of the software, so the attacks can be found.
JPEGsnoop can identify a picture’s information, if we change or edit the picture, these elements of the picture will change so that we can use it to know if this picture is an original one. For a defender, this tool will help him know more about his pictures whether they are counterfeited, edited, modified or not.
Reference
[1]http://forums.whirlpool.net.au/archive/1127492
[2]http://en.wikipedia.org/wiki/Facial_recognition_system
[3]http://baike.baidu.com/view/246859.htm
[4]http://www.enet.com.cn/eschool/zhuanti/photo/
[5]http://electronics.howstuffworks.com/cameras-photography/digital/digital-camera.htm
[6]http://computer.howstuffworks.com/laser-printer.htm
[7]http://www.webopedia.com/TERM/L/laser_printer.html
Video
[8]http://www.youtube.com/watch?gl=AU&hl=en-GB&v=W_Qdag5FdE8
Paper

Hi there I located your page by mistake when i was searching Msn for this subject, I have to say your blog is very helpful I also enjoy the layout, its amazing!
[回复]
I think one of your advertisements caused my internet browser to resize, you might want to put that on your blacklist.
[回复]
Thanks for an idea, you sparked at thought from a angle I hadn’t given thoguht to yet. Now lets see if I can do something with it.
[回复]
Beneficial info and excellent design you got here! I want to thank you for sharing your ideas and putting the time into the stuff you publish! Great work!
[回复]
My partner and I really enjoyed reading this blog post, I was just itching to know do you trade featured posts? I am always trying to find someone to make trades with and merely thought I would ask.
[回复]
great post, thanks for sharing
[回复]
Its like you read my mind! You appear to know so much about this, like you wrote the book in it or something. I think that you can do with some pics to drive the message home a bit, but instead of that, this is wonderful blog. A great read. I’ll certainly be back.
[回复]
Awesome message, I absolutely wait for posts of your stuff.
[回复]
Beneficial content, I must say i expect messages of your stuff.
[回复]
your websites are rather awesome!!!
[回复]
Amy 回复:
1月 11th, 2014 at 13:05
I enjoy reading thgourh your blog, your posts are generally really educational and in what way you put every thing away makes it simple to grasp. I don’t normally comment however I decided I will at the least we appreciate you doing a very good career. Appreciate it and make up the great work.
[回复]
car insurance 回复:
6月 28th, 2014 at 19:58
It’s a pleasure to find such rationality in an answer. Welcome to the debate.
[回复]
Does your site have a contact page? I’m having a tough time locating it but, I’d like to shoot you an email.
I’ve got some recommendations for your blog you might be interested in hearing. Either way, great blog and I look forward to seeing it expand over time.
[回复]
I’m very new to this and am fumbling my way through. Have just self published a book, Boarding School Boy, and am seeking ways to have it out in the market. Your option of having it reviewed appealed to me so I am trying to view how I go about it. To whom do I send a copy? How do I get members to read my book and post reviews.
[回复]
Chuckles 回复:
1月 14th, 2014 at 10:57
Yeah, that’s the tiectk, sir or ma’am
[回复]
88888 You do have a large amount of folks observing so that you definitely do want some wind to come back in.”. Your usage of the internet site suggests your arrangement for being sure by the Terms of Use..
[回复]
Hello There. I discovered your weblog the usage
of msn. That is a very neatly written article. I’ll be sure
to bookmark it and come back to learn more of your helpful info.
Thanks for the post. I’ll certainly comeback.
[回复]
Hey there just wanted to give you a quick heads up. The text in your content
seem to be running off the screen in Ie. I’m not sure if this is
a format issue or something to do with browser compatibility but I figured I’d post
to let you know. The design and style look great though! Hope you get the issue
solved soon. Cheers
Look at my webpage; 2013 専門店
[回复]
canada goose en ligne
[回复]
Youre so cool! I dont suppose Ive read anything like this prior to. So nice to come across somebody with some original thoughts on this subject. realy thank you for starting this up. this internet site is some thing that’s necessary on the internet, someone with a little originality. valuable job for bringing something new to the web!
[回复]
http://www.monton4cycling.com is the monton official retail web ,we are pro bicycle wear supplier and offer high quality cycle windbreaker at the lowest prices , buy monton bicycle clothing from our web ensure you 100% Satisfaction.
[回复]
I’m impressed by your writing. Are you a professional or just very knowledgeable?
[回复]
TYVM you’ve solved all my problems
[回复]
Such an impressive answer! You’ve beaten us all with that!
[回复]
No question this is the place to get this info, thanks y’all.
[回复]
That’s a sharp way of thinking about it.
[回复]
That’s a smart answer to a difficult question.
[回复]
Deadly accurate answer. You’ve hit the bullseye!
[回复]
Back in school, I’m doing so much learning.
[回复]
Great insight. Relieved I’m on the same side as you.
[回复]
This insight’s just the way to kick life into this debate.
[回复]
It’s about time someone wrote about this.
[回复]
It’s a pleasure to find someone who can think so clearly
[回复]
I thought I’d have to read a book for a discovery like this!
[回复]
Can I simply just say what a comfort to uncover an individual who actually knows what they’re talking about on the web. You definitely realize how to bring a problem to light and make it important. A lot more people really need to read this and understand this side of your story. It’s surprising you are not more popular since you certainly have the gift.
[回复]
You have the monopoly on useful information-aren’t monopolies illegal? ;)
[回复]
When you think about it, that’s got to be the right answer.
[回复]
Great common sense here. Wish I’d thought of that.
[回复]
Now I feel stupid. That’s cleared it up for me
[回复]
Frankly I think that’s absolutely good stuff.
[回复]
Great insight! That’s the answer we’ve been looking for.
[回复]
A good many valuables you’ve given me.
[回复]
That’s going to make things a lot easier from here on out.
[回复]
Furrealz? That’s marvelously good to know.
[回复]
That’s a posting full of insight!
[回复]
Help, I’ve been informed and I can’t become ignorant.
[回复]
You’re a real deep thinker. Thanks for sharing.
[回复]
This site is like a classroom, except I don’t hate it. lol
[回复]
That’s way more clever than I was expecting. Thanks!
[回复]
That’s a wise answer to a tricky question
[回复]
Thinking like that shows an expert’s touch
[回复]
Your’s is the intelligent approach to this issue.
[回复]
I’m quite pleased with the information in this one. TY!
[回复]
It’s a pleasure to find someone who can identify the issues so clearly
[回复]
That’s a quick-witted answer to a difficult question
[回复]
Keep these articles coming as they’ve opened many new doors for me.
[回复]
That’s a brilliant answer to an interesting question
[回复]
It’s great to read something that’s both enjoyable and provides pragmatisdc solutions.
[回复]
Yo, that’s what’s up truthfully.
[回复]
I’m not quite sure how to say this; you made it extremely easy for me!
[回复]
In the complicated world we live in, it’s good to find simple solutions.
[回复]
fmnaPY Thanks again for the blog.Really looking forward to read more. Fantastic.
[回复]
DANEMARK KROHNDEHLI JOIEKasimpasa se penche sur le cas du milieu de terrain offensif international danois Michael Krohn-Dehli (29 ans, Bröndby), également courtisé par l’Evian TGFC.
[回复]
Rattling great information can be found on blog.
[回复]
I really liked your article post.Thanks Again. Great.
[回复]
A round of applause for your article post.Really thank you! Awesome.
[回复]
I really liked your post.Really looking forward to read more. Great.
[回复]
Fantastic article post.Much thanks again. Cool.
[回复]
Very nice post and right to the point. I am not sure if this is actually the best place to ask but do you people have any thoughts on where to employ some professional writers? Thx
[回复]
I really like and appreciate your article.Thanks Again. Really Cool.
[回复]
I really enjoy the blog.Much thanks again. Cool.
[回复]
Wonderful beat ! I would like to apprentice while you amend
[回复]
Very informative blog article.Much thanks again.
[回复]
Wow, great blog post.Really thank you! Really Great.
[回复]
Appreciate you sharing, great blog post.Thanks Again. Fantastic.
[回复]
A big thank you for your blog post. Want more.
[回复]
Really appreciate you sharing this article. Really Cool.
[回复]
Say, you got a nice blog article. Want more.
[回复]
very good submit, i definitely love this website, keep on it
[回复]
This blog was how do I say it? Relevant!! Finally I ave found something that helped me. Kudos!
[回复]
Hey, thanks for the post.Really thank you! Keep writing.
[回复]
Thank you for your article.Really looking forward to read more.
[回复]
A round of applause for your blog.Really looking forward to read more. Awesome.
[回复]
Really enjoyed this article post.Really looking forward to read more. Cool.
[回复]
Really enjoyed this article post. Fantastic.
[回复]
Very neat blog article.Thanks Again. Keep writing.
[回复]
You need to participate in a contest for the most effective blogs on the web. I will advocate this website!
[回复]
Wanted to drop a remark and let you know your Feed isnt functioning today. I tried including it to my Bing reader account and got nothing.
[回复]
I truly appreciate this post. Really Cool.
[回复]
This blog was how do I say it? Relevant!! Finally I ave found something which helped me. Cheers!
[回复]
Im thankful for the blog post.Really thank you! Much obliged.
[回复]
louis vuitton handbags louis vuitton handbags
[回复]
Thanks so much for the post.Really looking forward to read more. Want more.
[回复]
Great, thanks for sharing this post.Really looking forward to read more. Much obliged.
[回复]
Perfect piece of function you have done, this internet site is actually cool with excellent details.
[回复]
You made some good points there. I looked on the internet for the issue and found most guys will go along with with your website.
[回复]
Very interesting subject, regards for posting.
[回复]
Some truly nice stuff on this web site , I it.
[回复]
This is very interesting, You are a very skilled blogger. I ave joined your feed and look forward to seeking more of your magnificent post. Also, I ave shared your site in my social networks!
[回复]
Thanks so much for the blog post.Really thank you! Really Great.
[回复]
Very neat article post.Thanks Again. Great.
[回复]
Its hard to find good help I am regularly proclaiming that its hard to get good help, but here is
[回复]
Appreciate you sharing, great blog article.Thanks Again. Really Great.
[回复]
Thanks for sharing, this is a fantastic blog article.Really looking forward to read more. Much obliged.
[回复]
It as not that I want to duplicate your web-site, but I really like the design. Could you let me know which theme are you using? Or was it especially designed?
[回复]
Well I truly enjoyed reading it. This information procured by you is very helpful for proper planning.
[回复]
This is one awesome post.Really looking forward to read more. Will read on
[回复]
Im obliged for the blog article.Really thank you! Great.
[回复]
I really liked your article.Really looking forward to read more. Keep writing.
[回复]
Say, you got a nice blog article.Really thank you! Will read on
[回复]
I was looking for the report in Yandex and suddenly came across this page. I found a little information on my topic of my report. I would like more, and thanks for that..!
[回复]
I really like and appreciate your post.Really looking forward to read more.
[回复]
Appreciate you sharing, great blog post.Really thank you! Want more.
[回复]
It is in reality a great and useful piece of info. I am satisfied that you shared this helpful tidbit with us. Please keep us informed like this. Thanks for sharing.
[回复]
This unique blog is obviously educating additionally informative. I have picked up a lot of handy advices out of this blog. I ad love to come back over and over again. Thanks!
[回复]
Looking forward to reading more. Great post.Much thanks again. Really Cool.
[回复]
I really liked your blog.Really looking forward to read more. Cool.
[回复]
It as onerous to search out educated individuals on this topic, however you sound like you know what you are speaking about! Thanks
[回复]
Really appreciate you sharing this post. Want more.
[回复]
May you please prolong them a bit from next time? Thanks for the post.
[回复]
Looking forward to reading more. Great post. Really Great.
[回复]
It as hard to come by knowledgeable people in this particular topic, however, you seem like you know what you are talking about! Thanks
[回复]
It as hard to come by well-informed people in this particular subject, however, you sound like you know what you are talking about! Thanks
[回复]
I was suggested this blog by my cousin. I am not sure whether this post
[回复]
I went over this web site and I conceive you have a lot of great info, saved to bookmarks (:.
[回复]
You got a very superb website, Gladiolus I detected it through yahoo.
[回复]
This is very interesting, You are a very skilled blogger. I ave joined your rss feed and look forward to seeking more of your magnificent post. Also, I ave shared your web site in my social networks!
[回复]
Some really good content on this web site , thankyou for contribution.
[回复]
Looking forward to reading more. Great blog post.Much thanks again. Keep writing.
[回复]
Your style is unique compared to other people I have read stuff from. I appreciate you for posting when you have the opportunity, Guess I will just bookmark this web site.
[回复]
This is a topic that is near to my heart Best wishes!
[回复]
This very blog is definitely interesting and also informative. I have picked up a lot of useful tips out of this source. I ad love to return over and over again. Thanks a bunch!
[回复]
I truly appreciate this post.Much thanks again. Fantastic.
[回复]
Thanks so much for the blog article. Will read on…
[回复]
Thanks again for the blog article.Really looking forward to read more. Will read on
[回复]
Im no pro, but I consider you just crafted the best point. You certainly know what youre talking about, and I can seriously get behind that. Thanks for staying so upfront and so truthful.
[回复]
I truly appreciate this article.Really thank you! Fantastic.
[回复]
Of course, what a fantastic website and informative posts, I definitely will bookmark your site.All the Best!
[回复]
instances, an offset mortgage provides the borrower with the flexibility forced to benefit irregular income streams or outgoings.
[回复]
thing. Do you have any points for novice blog writers? I ad definitely appreciate it.
[回复]
stumbleupon everyday. It as always useful
[回复]
Major thanks for the article.Really looking forward to read more.
[回复]
Looking forward to reading more. Great blog post.Really looking forward to read more. Really Cool.
[回复]
Very good article.Really looking forward to read more. Cool.
[回复]
Thanks for sharing this first-class post. Very inspiring! (as always, btw)
[回复]
Thanks-a-mundo for the blog article.Really thank you! Will read on
[回复]
You made some clear points there. I did a search on the issue and found most individuals will go along with with your website.
[回复]
Wow! Thank you! I always wanted to write on my website something like that. Can I include a fragment of your post to my website?
[回复]
Appreciate you sharing, great blog article.Really looking forward to read more. Much obliged.
[回复]
Very good article post.Really thank you! Fantastic.
[回复]
Thanks again for the post.Really looking forward to read more.
[回复]
What are the laws as to using company logos in blog posts?
[回复]
Say, you got a nice article.Much thanks again. Keep writing.
[回复]
Wonderful post! We will be linking to this great content on our site. Keep up the good writing.
[回复]
some pics to drive the message home a little bit, but instead of that, this is great blog.
[回复]
Website We Recommend You made some fine points there. I did a search on the matter and found most people will consent with your blog.
[回复]
Thankyou for helping out, excellent information.
[回复]
Im grateful for the blog article.Really looking forward to read more. Keep writing.
[回复]
the minute but I have saved it and also included your RSS feeds, so
[回复]
Muchos Gracias for your blog article.Much thanks again. Much obliged.
[回复]
The data mentioned in the article are a number of the best offered
[回复]
Hey, thanks for the article. Really Cool.
[回复]
Pink your website post and cherished it. Have you at any time imagined about guest putting up on other relevant weblogs comparable to your website?
[回复]
Some really quality articles on this web site , bookmarked.
[回复]
newest information. Also visit my web-site free weight loss programs online, Jeffery,
[回复]
Thanks so much for the post.Thanks Again. Really Cool.
[回复]
Appreciate you sharing, great article. Really Great.
[回复]
Major thankies for the article.Really looking forward to read more. Really Cool.
[回复]
of hardcore SEO professionals and their dedication to the project
[回复]
Woh I enjoy your content, saved to fav!.
[回复]
Looking forward to reading more. Great article post.Much thanks again. Awesome.
[回复]
This Swimwear is named as Ed Durable Men as swimwear. It
[回复]
This excellent website really has all the information and facts I wanted about this subject and didn at know who to ask.
[回复]
Major thanks for the article post. Keep writing.
[回复]
I recommend them for sure What type of images am I аАааАТаЂТlegally a allowed to include in my blog posts?
[回复]
Some really select content on this site, saved to fav.
[回复]
I am so grateful for your article.Thanks Again. Will read on…
[回复]
Simply a smiling visitant here to share the love (:, btw great pattern.
[回复]
Thanks for some other fantastic post. Where else may anyone get that kind of information in such an ideal method of writing? I have a presentation next week, and I am at the search for such info.
[回复]
Thanks so much for the article post. Want more.
[回复]
Thank you pertaining to sharing the following great subject matter on your website. I ran into it on google. I am going to check to come back after you publish additional aricles.
[回复]
I truly appreciate this blog article.Really thank you! Want more.
[回复]
Thanks a lot for the post.Really thank you! Keep writing.
[回复]
Pretty! This has been an extremely wonderful article. Thanks for providing these details.
[回复]
Major thanks for the blog post.Really looking forward to read more. Really Cool.
[回复]
Really informative article post.Much thanks again. Really Cool.
[回复]
It as in reality a nice and useful piece of info. I am happy that you shared this useful tidbit with us. Please keep us up to date like this. Thanks for sharing.
[回复]
themselves, especially contemplating the reality that you simply might have completed it if you ever decided. The pointers also served to provide an excellent technique to
[回复]
Looking forward to reading more. Great blog.Really thank you! Will read on…
[回复]
J aadmire cette photo neanmoins j aen ai deja entendu certains nouveaux de meilleures qualifications?
[回复]
I wanted to thank you for this fantastic article, I certainly loved each and every small bit of it. I ave bookmarked your web site to look at the newest stuff you post.
[回复]
Wonderful goods from you, man. I have take
[回复]
Usually I do not read post on blogs, but I wish to say that this write-up very pressured me to check out and do it! Your writing taste has been amazed me. Thank you, quite nice article.
[回复]
Merely wanna input that you ave got a very great web page, I enjoy the style and style it seriously stands out.
[回复]
It is really a nice and helpful piece of info. I am glad that you shared this helpful info with us. Please keep us up to date like this. Thank you for sharing.
[回复]
Rtl horoscope haas horoscope poisson du jour femme
[回复]
I value the blog post.Really looking forward to read more. Will read on
[回复]
Very good blog article. Great.
[回复]
This awesome blog is definitely cool and informative. I have found a bunch of helpful tips out of it. I ad love to visit it again soon. Thanks!
[回复]
Looking forward to reading more. Great blog.Thanks Again. Want more.
[回复]
So why you dont have your website viewable in mobile format? Won at view anything in my own netbook.
[回复]
You might be my role models. Many thanks to the write-up
[回复]
Its hard to find good help I am regularly proclaiming that its difficult to get quality help, but here is
[回复]
Just Browsing While I was browsing today I saw a excellent article about
[回复]
Thanks for sharing this very good piece. Very inspiring! (as always, btw)
[回复]
Im obliged for the blog.Much thanks again. Cool.
[回复]
It as not that I want to copy your web site, but I really like the style. Could you tell me which theme are you using? Or was it tailor made?
[回复]
Of course, what a great site and illuminating posts, I definitely will bookmark your site.Have an awsome day!
[回复]
Stupid Human Tricks Korean Style Post details Mopeds
[回复]
Wow, great post.Really thank you! Great.
[回复]
Thanks again for the blog.Thanks Again. Keep writing.
[回复]
Im thankful for the blog post.Really thank you! Want more.
[回复]
Utterly indited content, appreciate it for selective information. Life is God as novel. Let him write it. by Isaac Bashevis Singer.
[回复]
Thanks to this blog I deepened my knowledge.
[回复]
Really enjoyed this post. Awesome.
[回复]
Some genuinely select blog posts on this internet site , saved to fav.
[回复]
Appreciate you sharing, great blog article.Really thank you! Cool.
[回复]
http://in100slots.ru
[回复]
http://joybetsonline.ru
[回复]
http://joygamingz.ru
[回复]
http://bingoslotz24.ru
[回复]
http://bingobets24.ru
[回复]
http://bingomachine24.ru
[回复]
http://bingobetz24.ru
[回复]
http://powerspinz24.ru
[回复]
http://dumskaya.net/user/dwarowican/
Дадим Вам декоративные бетонные парканы которые будут служить для вас 40 лет и более. Абсолютно все работы готовы сделать под ключ без дополнительных переплат и потери времени. Уже после подписания заказа Ваш паркан будет установлен у вас уже через 10 дней. Без новых взносов и не указных ранее платежей, все что обсудили – стоимость остается без изменений. Такие предложения обеспечиваю стажем деятельности с 2006 года, с этого периода мы только растем благодаря положительным рекомендациям наших покупателей.
[回复]
Доводим Вас до сведения об одобрении выдать Вам некую сумму. Рекомендуем сейчас Обязательно оформить детали зайдя на основную страницу платежного сервиса в течение 5 часов.Не пропустите момент! пока Ваш доступ в систему не аннулирован!Переход на страницу: http://tinyurl.com/scusatte
[回复]
“Deepsleep” How Long Is The Trial Days
https://bit.ly/2QsK1hM
[回复]